


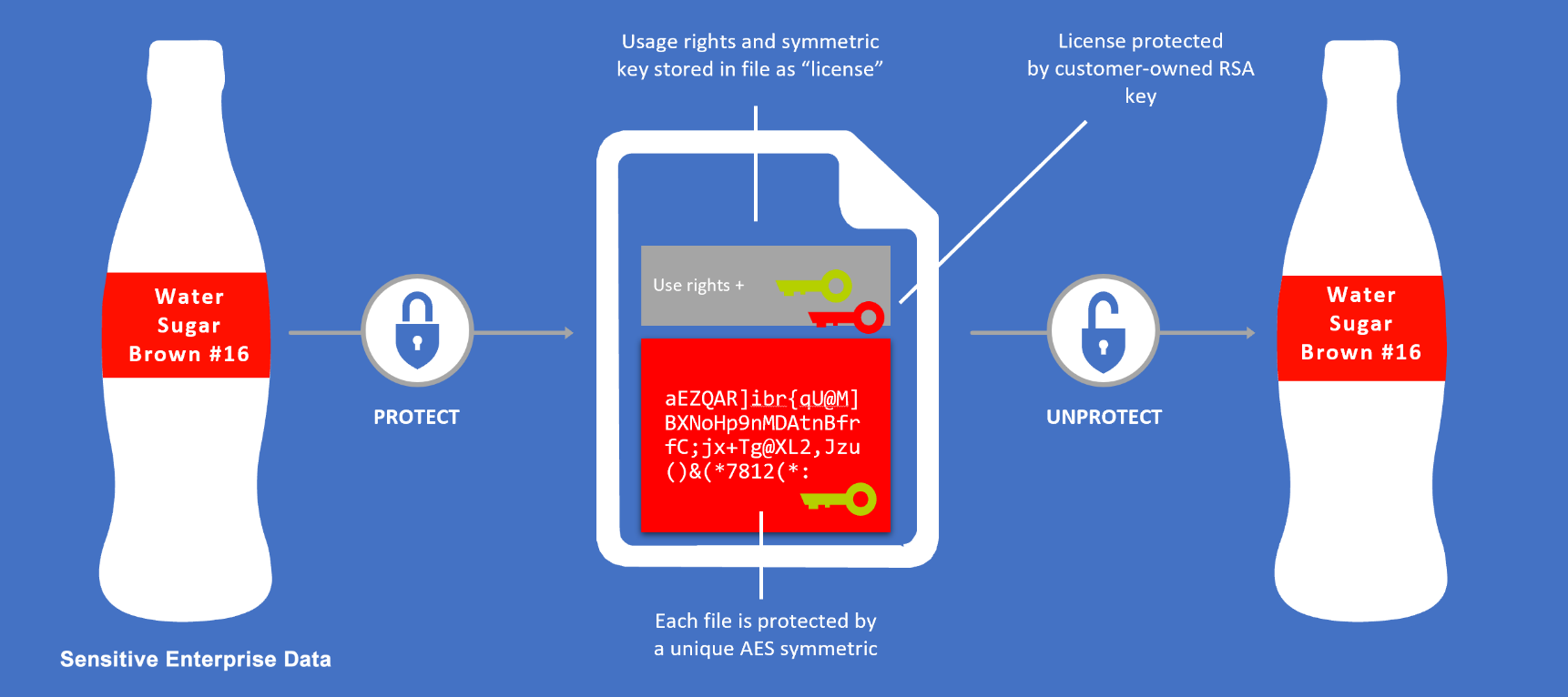
Azure Rights Management System uses encryption, identity, and authorization policies to help secure your files and email, and it works across multiple devices—phones, tablets, and PCs. Information can be protected both within your organization and outside your organization because that protection remains with the data, even when it leaves your organization’s boundaries.
Organizations no longer operate within their own perimeter. Data is travelling between users, devices, apps and services more than ever before. And protecting your perimeter, users or devices does not guarantee the protection of your data as it travels outside of corporate boundaries.
Protect data at the time of creation or modification from the source.
Once data is labelled, optional protection can be applied based on the requirement.
Data protection controls are integrated into Office and common applications.
This provides one-click options to classify data they are working currently
Persistent protection with your users as well as with your customers and partners.
Users can define who can access data and what they can do with it based on the use of rights policy.
Users can track activities on shared data and revoke access if necessary.
IT can use powerful logging and reporting to monitor, analyze, and reason over shared data.
There is control over your data inside your network boundaries. Once it leaves your network, you lose the ability to protect or track it.
Rights Management System (RMS) allows you to classify and add security directly to your sensitive data so that its always protected and identifiable.
According to the Identity Theft Resource Center (ITRC), from January 2005 to September 2019 many agencies and companies suffered 10,939, data breach instances and 1,655,387,106 of records exposed.
Data breaches in the U.S. are vastly more expensive – costing USD 8.19 million (about ₹56.46 crores), or more than double the average for worldwide companies stated in the study conducted by the Ponemon Institute.
As per THG Publishing (thehindu.com), on an average, 35,636 records were compromised in a data breach in India that ranked 15th in terms of the total cost of a breach. Data breaches cost organizations in India about ₹12.8 crores on average between July 2018 and April 2019, according to a report sponsored by tech giant IBM.
Other Key Features:
SUCCESS STORIES
Having seamless exchange of information not just within our company but also with our customers and partners, at the same protecting our data had always been a big challenge for us. With the help of Cloud 9's expertise, we switched to Right Management System which provides us both; a smooth flow of information within and outside of the organization and full protection of our sensitive information. We are really pleased with professionalism and expertise of Cloud 9 and looking forward to a long-term relationship as our trusted advisor.
AVID KHAN
IT HEAD, NAVNIT MOTORS PRIVATE LIMITED
Bring greater focus to sales and marketing with DynamicUnified Security, Compliance and monitoring for Containers and Micro services on Azure s 365
Cloud 9 ’s Complimentary Cloud readiness Assessment understands your business goals and recommends most suitable cloud architecture.


